Client VPN users may access all subnets within the network by default. In order to control or restrict access for Client VPN users, firewall rules should be implemented.
Layer 3 firewall rules are a powerful tool for permitting and denying Client VPN traffic. Although Client VPN users are considered part of the LAN, network administrators may see a need for limiting overall access. Firewall rules can be used to limit access for VPN users to specific addresses/ports or ranges of addresses. Such as allowing access to most information, but denying access to sensitive resources to VPN users.
In the following example, we will be creating a Client VPN subnet and configuring rules that will permit and deny access based a several parameters.
- Configuring Client VPN subnet
- Configuring Addressing & VLANs subnet(s)
- Configuring Firewall Rules
Configuring Client VPN subnet
The Client VPN subnet is configured via Configure > Client VPN. Take note of this network address as it will be used to implement Firewall rules for controlling traffic related to that subnet. In the following scenario, our Client VPN subnet will be (172.16.1.0/24)
Client VPN Last updated; Save as PDF Most popular; Highest rated; Recently updated; Recently added; Allow remote users to securely access files and services on the network through an encrypted tunnel over the Internet. Meraki Client VPN. On Apr 16, 2015 at 21:19 UTC. Solved General Networking. Next: can't enable trunking. Get answers from your peers along with. The Meraki MX64 provides unlimited VPN users We love the Cisco Meraki VPN at Telnexus. The MX security appliance is a powerful guardian and gateway between the wild Internet and your private Local Area Network (LAN).
Configuring Addressing & VLANs subnet(s)
Subnets local to the MX are configured via Configure > Addressing & VLANs. Below is an example depicting an MX that has VLANs enabled. Two subnets are present: (192.168.10.0/24) and (192.168.20.0/24). Both of these subnets will be accessible by users who establish a successful Client VPN session.
Additionally, subnets made known to the MX via Static LAN routes will also be available to the Client VPN subnet.These subnets are also configured via Configure > Addressing & VLANs.
As shown below, the non-local subnet is 10.0.1.0/24, and will be pointed to a router with the address of 192.168.10.2.
Configuring Firewall Rules
Navigating to Configure > Firewall, note that the default settings permit all outbound traffic. This allows all subnets to communicate, including the client VPN network. Outbound rules also apply to Inter-VLAN Routing.
Outbound rules should be implemented to control which subnets Client VPN users may access. These rules are processed numerically, like an ACL, starting with Rule #1. Once a rule is matched, no further rules will be processed. Thus, the Rule number is essential.
Example 1
In the following example, the entire Client VPN subnet (172.16.1.0/24) will only have access to Subnet 1 and Subnet 2. The Client VPN subnet will not have access to Non-local Subnet 1.
Only a single rule denying all traffic from the Client VPN subnet to the non-local subnet is needed since there is an implicit 'Allow' rule at the end that permits all other outbound traffic.
Example 2

In this next example, VPN clients are permitted to access HTTPS (secure web) and DNS servers on a LAN subnet, but all other access is denied.
There are many combinations of firewall rules available for configuration. As a general rule of thumb, configure rules that apply to a specific port/destination first, before configuring a rule that applies to the subnet as a whole. Please be sure to test and verify all firewall rules along the way to ensure proper access.
We love the Cisco Meraki VPN at Telnexus. The MX security appliance is a powerful guardian and gateway between the wild Internet and your private Local Area Network (LAN). Here are the abbreviated instructions on how to connect your PC or Mac back to home base.
Meraki Documentation Link
For complete instructions as well as instructions for other versions of Windows and MacOS as well as Linux, iOS and Android, please consult the official Meraki documentation:
Meraki Client Vpn Multifactor Authentication

VPN Credentials
You should receive the following bits of information from your administrator:
- IP address or hostname of your VPN server
- A “Preshared Key”
- Your username
- Your password
Windows 10 Meraki VPN Setup
Here are the basic steps:
- Go to Settings->Network->VPN
- Create a new L2TP/IPsec VPN
- Name it “My Company VPN”
- Enter the Server Address
- Enter the Preshared Key
- Enter your Username and Password
- Complete the new VPN wizard
- Select Adapter Options
- Right-click on your new VPN, select Properties
- Click on the Security tab, and then click “Allow these protocols”
- Under “Allow these protocols” make sure “Unsecured password (PAP)” is the only one checked
- Click OK to close the Properties box
- Right-click on the new VPN icon and select Connect
- Click Connect (again) in the Settings->Network->VPN window
For full documentation with screenshots please check the official Meraki documentation.

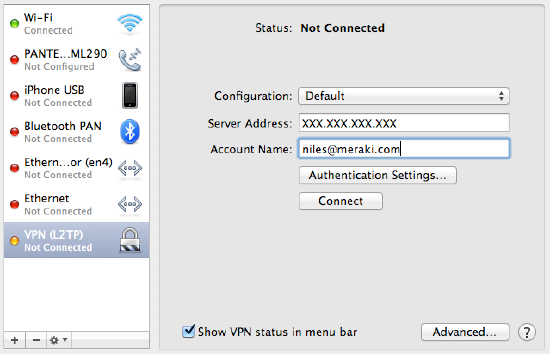
MacOS Meraki VPN Setup
Here are the basic steps:
- Open System Preferences > Network from Mac applications menu. Click the “+” button to create a new service, then select VPN as the interface type, and choose L2TP over IPsec from the pull-down menu.
- Enter your server address in Server Address
- Enter your Meraki username in Username
- Click Authentication Settings
- Enter your Password in box the User Authentication section
- Enter your Preshared Key in the Shared Secret box
- Click OK to close the Authentical panel
- Click Apply to save your settings
- Click Connect to activate your VPN

Meraki Client Vpn Ports
For full documentation with screenshots, please check the official Meraki documentation.
Related Posts

Comments are closed.