This walkthrough will describe how to use your Cisco ASA5505 as a VPN server for a remote client. The remote client doe not need to have an 5505 as a VPN endpoint, it only needs to have the Cisco VPN Client software installed.
- Cisco Asa Vpn Client
- Cisco Asa Vpn Client Windows 10
- Cisco Asa Ssl Vpn Configuration
- Cisco Asa Vpn Client Certificate Authentication
- Anyconnect Client Asa Version Compatibility
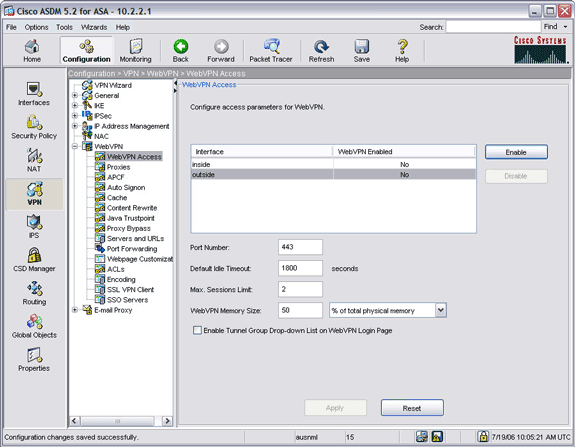
To configure the ASA5505, first log into it using the Cisco ASDM.
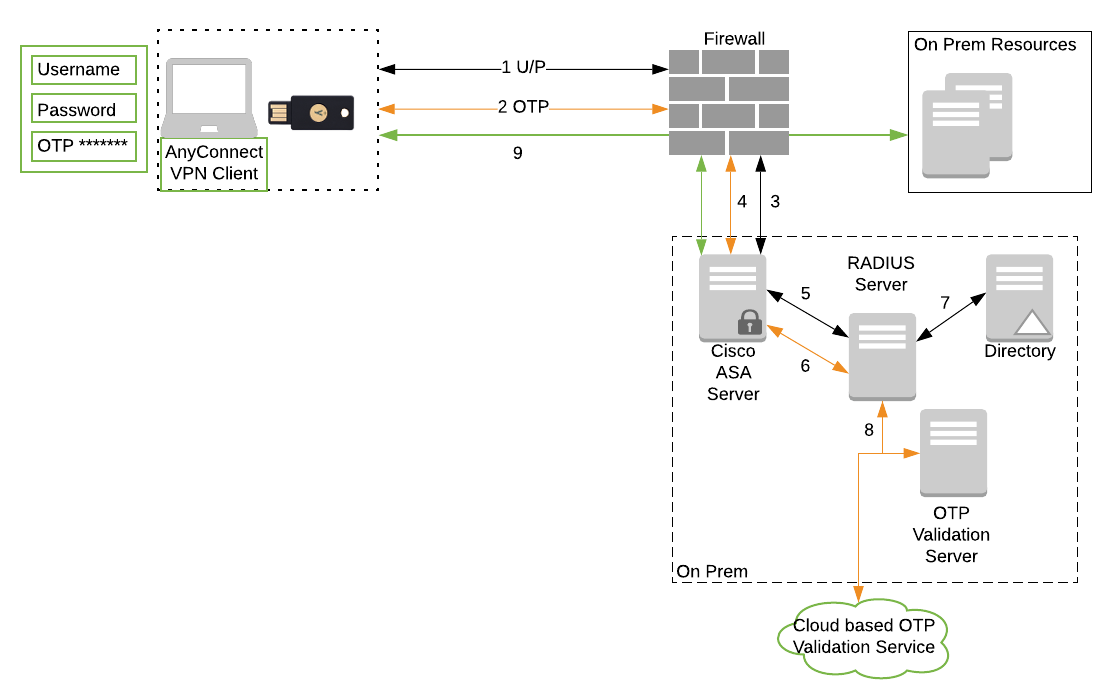
Azure Multi-Factor Authentication Server (Azure MFA Server) can be used to seamlessly connect with various third-party VPN solutions. This article focuses on Cisco® ASA VPN appliance, Citrix NetScaler SSL VPN appliance, and the Juniper Networks Secure Access/Pulse Secure Connect Secure SSL VPN appliance. The Cisco AnyConnect Secure Mobility Client provides secure SSL and IPsec/IKEv2 connections to the ASA for remote users. Without a previously-installed client, remote users enter the IP address in their browser of an interface configured to accept SSL or IPsec/IKEv2 VPN connections. I am trying to set up an Remote-VPN IPsec ikev1 from a Windows 10 built in VPN-client to a Cisco asa 5505, using a L2TP/IPsec runnel with a Pre-shared key and xAuth. After some struggle, I manage to complete both IPsec Phase 1 and Phase 2. With the clientless SSL solution in the Cisco ASA firewall you will have a good complent to the client based VPN solutions such as the IPSec client.
- Click the “Wizards” drop down, select “VPN Wizard.”
- Select “Remote Access,” click Next.
- Select “Cisco VPN Client,” click Next
- Select “Pre-shared key,” then fill in what I’m going to call your “VPN Connection Password.” This will be saved in the client and should be as long and secure as possible.
- Tunnel Group Name: Enter what I’m going to call your “VPN Connection Username,” and Click Next.
- Select “Authenticate using the local user database,” click Next.
- Create a username and password for each VPN user, click Next.
- Click “New…” to create a new VPN IP pool. You can do whatever you want here, but here is my suggestion:
- Name: VPNUsers
- Starting IP Address: 192.168.15.194
- Ending IP Address: 192.168.15.220
- Subnet Mask: 255.255.255.224
- Click “OK.”
- Click Next.
- Fill in DNS and WINS for your outside network and Click Next.
- IKE Policy defaults are fine, click Next.
- IPSec defaults are fine, click Next.
- Leave NAT Settings blank, but check “Enable Split tunneling” at the bottom and click Next.
- Click Finish.
One more step, without this you won’t be able to connect to anything besides the internal network when you are connected to the VPN.
- Click “Configuration” at the top of the screen.
- Click “VPN” on the left side of the screen.
- Under “General,” click “Group Policy.”
- Click the Group Policy that corresponds to the one you defined during the Wizard, and click the Edit button.
- Click the Client Configuration Tab.
- Click the “Manage” button next to Split Tunnel Network List.
- Double click the Entry under the Standard ACL tab.
- Change the IP address and Netmask to match that of your internal network, the subnet where your servers are located.
- Click OK, OK, OK and finally: Apply.
Now that we’ve done all that, we should save it from working memory into the flash. I like to do a reboot while I do this, and we can do it using the Cisco ASDM!
- Click Tools and select System Reload.
- Be sure to change the radio button at the top to Save the running configuration at the time of reload.
- Click “Schedule Reload,” Yes, and Exit ASDM.
To connect your new VPN, you’ll need the Cisco VPN Client. I’m using version 4.6.
- Install the Cisco VPN Client.
- Click “New.”
- Connection Entry: Name of the VPN connection. I used the same thing I put in for the Tunnel Group Name (VPN Connection Username), but you can use whatever you want.
- Host: The IP address or DNS name of the VPN Server.
- On the Authentication Tab, make sure “Group Authentication” is selected.
- Name: Put whatever you put for Tunnel Group Name (VPN Connection Username).
- Password: put in your “Pre-shared Key” VPN (Connection password).
That’s it! Hit Save.
To connect, double-click the connection entry you just created.
Enter your username and password, which we defined users on the Cisco ASA5505 device during the VPN Wizard.
Done and Done!
- 3Gateway Configuration
- 4Client Configuration
- 4.3Authentication Tab
Introduction
This guide provides information that can be used to configure a Cisco PIX/ASA device running firmware version 7.x to support IPsec VPN client connectivity. If you have a PIX device running firmware version 6.x, please consult the HowtoCiscoPix. The Shrew Soft VPN Client has been tested with Cisco products to ensure interoperability.
Overview
The configuration example described below will allow an IPsec VPN client to communicate with a single remote private network. The client uses the pull configuration method to acquire the following parameters automatically from the gateway.
- IP Address
- IP Netmask
- DNS Servers
- DNS Default Domain Suffix
- DNS Split Network Domain List
- WINS Servers
- PFS Group
- Remote Network Topology
- Login Banner
Gateway Configuration
This example assumes you have knowledge of the Cisco ASA gateway command line configuration interface. For more information, please consult your Cisco product documentation.
Interfaces
Two network interfaces are configured. The outside interface has a static public IP address of 1.1.1.20 which faces the internet. The inside interface has a static private IP address that faces the internal private network. The default gateway is configured as 1.1.1.3 via the outside interface.
Access List
An access lists must be configured to define the IPSec policies. This is expressed with the source matching the local private network(s) and the destination matching any as the VPN client address will be assigned by the gateway.
Address Pool
The IP address pool must be configured. Clients will be assigned private network addresses from a pool of 10.2.20.1-10.2.20.126.
User Authentication
User authentication must be configured to support IKE extended authentication ( XAuth ). In this example, we use define user accounts locally on the ASA. It is possible to pass this authentication to a radius or an LDAP account server using the Cisco AAA authentication mechanism. For more information, please consult your cisco product documentation.
IPsec Parameters
A transform set and dynamic IPsec crypto map must be configured to support client VPN connections. The dynamic crypto map is then assigned to a standard crypto map and bound to the outside ( public ) interface.
ISAKMP Parameters
The ISAKMP protocol must be enabled on the outside ( public ) interface and an ISAKMP policy must be configured. NAT Traversal is also enabled to allow clients to communicate effectively when their peer address is being translated. The keep alive packet rate is set to 20 seconds.
Group Policy
A group policy must be configured to provide the client with dynamic configuration information.

Tunnel Group
A tunnel group must be configured to define the VPN Client tunnel parameters. It is created using the type ipsec-ra for IPsec remote access. The client uses the tunnel group name as its FQDN identity value and the tunnel group pre-shared-key as its pre-shared key value.
Cisco Asa Vpn Client
Client Configuration
The client configuration in this example is straight forward. Open the Access Manager application and create a new site configuration. Configure the settings listed below in the following tabs.
General Tab
The Remote Host section must be configured. The Host Name or IP Address is defined as 10.1.1.20 to match the ASA outside ( public ) interface address. The Auto Configuration mode should be set to ike config pull.
Phase 1 Tab
The Proposal section must be configured. The Exchange Type is set to aggressive and the DH Exchange is set to group 2 to match the ASA ISAKMP policy definition.
Authentication Tab
Cisco Asa Vpn Client Windows 10
The client authentication settings must be configured. The Authentication Method is defined as Mutual PSK + XAuth.
Local Identity Tab
The Local Identity parameters are defined as Fully Qualified Domain Name with a FQDN String of 'vpnclient' to match the ASA tunnel group name.
Remote Identity Tab
The Remote Identity parameters are set to IP Address with the Use a discovered remote host address option checked to match the ASA ISAKMP identity parameter.
Credentials Tab
The Credentials Pre Shared Key is defined as 'mypresharedkey' to match the ASA tunnel group pre-shared-key.
Known Issues
Cisco gateways support a proprietary form of hybrid authentication which does not conform to RFC draft standards. At this time the Shrew Soft VPN Client does not support this authentication mode. We hope to add support for this in the future.
Cisco Asa Ssl Vpn Configuration
Resources
Cisco Asa Vpn Client Certificate Authentication
Media:Ciscoasa.cfg.txt
Media:Ciscoasa.vpn.txt
Anyconnect Client Asa Version Compatibility

Comments are closed.